Enterprises Face Rapidly-Rising Hybrid Cloud and Web Threats
Last month, here at CMS-Connected, we discussed the primary business outcomes for  organizations that reap the benefits of moving from the legacy ECM solutions to the cloud-based content management services in the article entitled Digital Enterprises Get Their Head into the Cloud. Today, we will discuss one of the biggest barriers to cloud adoption: Security. A new study published yesterday by Netskope introduced a new concept of a hybrid cloud and web threats in its Q1 2017 cloud security review. The cloud security provider, Netskope, defines this hybrid threat as malware that attacks a system or a user through a hybrid of both cloud and web services.
organizations that reap the benefits of moving from the legacy ECM solutions to the cloud-based content management services in the article entitled Digital Enterprises Get Their Head into the Cloud. Today, we will discuss one of the biggest barriers to cloud adoption: Security. A new study published yesterday by Netskope introduced a new concept of a hybrid cloud and web threats in its Q1 2017 cloud security review. The cloud security provider, Netskope, defines this hybrid threat as malware that attacks a system or a user through a hybrid of both cloud and web services.
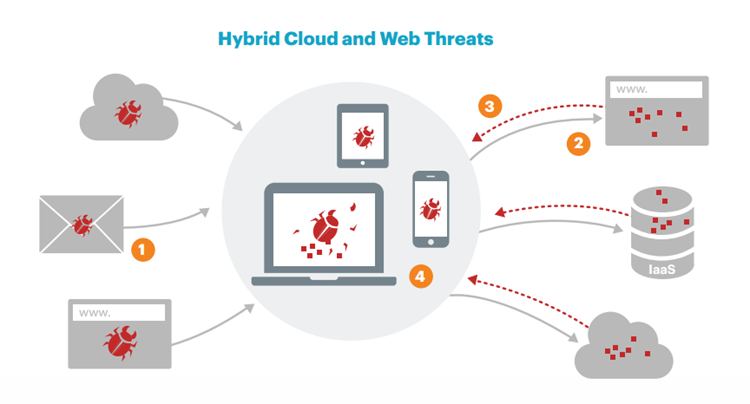
This kind of threat has a very underhanded tactic to sneak into your device and system. For instance, as a user, you have an initial malware on your device, and you are downloading a compromised application or infected file from Dropbox or Amazon AWS. You do not know that it is compromised or infected because they bypass security restrictions of your security solution as most of the time, those solutions detect either the web component or only the cloud part. However, in this attacking scenario, each environment has just a portion of fragmented threats, and each fragment is innocuous before congregating thus they wouldn’t be detected at first. Then, the initial malware decrypts and assembles the fragments to execute a system attack. “How did I get the initial malware?” you may ask. The study cites a couple of different scenarios for that. Getting malicious phishing email or downloading directly from a cloud storage service link shared by others can result in the initial malware infection, or this can be accomplished through simply visiting compromised websites. Now that websites are utilizing APIs more than ever to fetch content, especially ads, from other websites and cloud services, the study suggests that the number of this kind of cross-category attack will increase. Here’s an illustration created by Netskope to demonstrate how the attack is executed:
-
Malware infects user device via phishing email, compromised website, and cloud service with an infected file, etc.
-
Once the malware is downloaded, it calls to various services like websites, deletes cloud storage services, or even IaaS servers to download fragments of malicious code.
-
Malicious fragments are downloaded onto the device with security solutions seeing these downloads as innocuous as they haven’t been pieced together yet.
-
Initial malware decrypts and compiles the downloaded fragments to start an attack or whatever functions the malicious code is supposed to perform.
Therefore, enterprises should adopt context-aware security solutions and controls as they result in more accurate security decisions that are capable of supporting dynamic business and IT environments. Last year, during the Gartner Security & Risk Management Summit 2016, the top 10 technologies for information security were highlighted. One of those was intelligence-driven security operations center orchestration solutions. Gartner believes that an intelligence-driven security operations center (SOC) with an adaptive architecture and context-aware components can meet the challenges of the new "detection and response" paradigm. Another solution that may address this threat is a remote browser. According to Gartner, isolating the browsing function from the rest of the endpoint and corporate network can keep malware off of the end user's system.
The Vast Majority of Cloud Services Not Enterprise-Ready
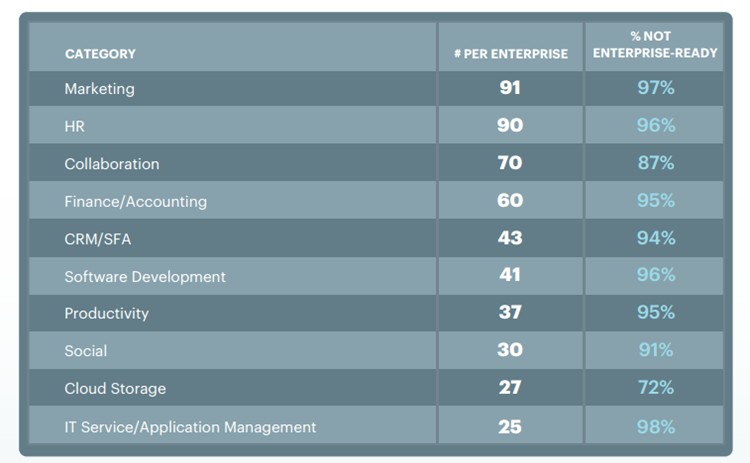
In Netskope’s previous report published in April 2017, it is cited that the average enterprise uses 91 marketing cloud services, and sadly, 94 percent of all cloud apps demonstrated in Netskope’s chart below are not enterprise-ready which means that they do not meet enterprise-level security and compliance requirements.
The enterprise-readiness of cloud services are not the only problem, as many enterprises that use cloud services to enable their employees to collaborate through sharing, editing and updating files on the cloud do not have a comprehensive security protocol to protect sensitive information within the shared files. As a result, this situation leads to increased chances of sensitive data loss through violations of data loss prevention (DLP) activities. Netskope concluded that webmail has the highest occurrence of the policy-violating activity. The report also noted that DLP violations can differ, giving examples of improper downloading of a non-public press release and theft of customer data from CRM by a departing employee.
Security is an issue for organizations that concerns not only internal but also external shareholders. In fact, 51 percent of Global Citizens with internet access are discouraged by the lack of trust online, choosing to not engage in online transactions due to privacy and security concerns, a new Ipsos survey for the Centre for International Governance Innovation has found. Therefore, when organizations are assessing a digital experience management system, security should always stay on the top of their criteria in order to maintain their brand integrity across all the digital touchpoints. Organizations also should ensure that all legally mandated content is present on their site, including data protection, privacy policies, terms and conditions, intellectual property protection and corporate disclaimers, while maintaining brand style and the editorial standards.
Online retailers, for instance, should invest more in new technology with built-in security protocols and authentication systems. It is important to stay on top of the new technology when it comes to data security of your organizations and your customers as the software written years ago can no longer prevent a data breach as it was developed to meet a certain need at the time, and most likely, things have moved on since then. Karsten Lund, a conversion specialist, discovered a 32% increase in conversions with the presence of a trust badge on the site. Rubbing off trust on an e-commerce site is a must for every online retailer. To that point, the familiar logos from external accreditors such as McAfee, Verisign, Paypal, BBB, and TRUSTe can assure prospects that the website is safe to hand over their credit card information. More importantly, placing a privacy policy on your website, stating that their information is in safe hands and elaborating clearly on the use of any information gathered to inform your customers can definitely make a difference. A comprehensive privacy policy should include at least what information is collected, how this information is used, and how this information is shared. Besides all these, a Secure Sockets Layer (SSL) button also eases their fears.
My POV
Nearly 1 million new malware threats are released each day, and cyber criminals get unauthorized access to your site to steal sensitive data such as credit card information through that malware. As we all know, the importance of creating a collaborative environment around integrated workflows, business processes, data streams, and applications is getting bigger and bigger within organizations. However, keeping track of what content is seen by whom has become one of the major challenges for enterprises dealing with booming collaboration and document services, considering 15.8% of documents in cloud file sharing services have sensitive information. Unfortunately, an alarming amount of those files shared can be seen by anyone in the organization without needing any specific permission. More importantly, a concerning proportion of shared documents can even be found through search engines. Therefore, while taking advantage of this emerging technology, it is also extremely critical to maintain sensitive content security with context-aware identification, filtering, and classification.
Before ensuring customers and employees that their information is in safe hands and their data hasn’t been compromised, first, organizations must make sure they do not use a malware-infected website or system. To detect and expel malware from their website, adopting an intelligence-driven context-aware security solution may reduce the risks.

Venus Tamturk
Venus is the Media Reporter for CMS-Connected, with one of her tasks to write thorough articles by creating the most up-to-date and engaging content using B2B digital marketing. She enjoys increasing brand equity and conversion through the strategic use of social media channels and integrated media marketing plans.