Identity & Access Management Systems are on the Rise
Digital transformation involves different thinking, innovation, a modification in leadership & new business models and incorporating digital strategy into all aspects of the business to improve the experience of your organization’s employees, customers, suppliers, and partners. To build those new, innovative company cultures, business models, and digital strategies, organizations need a solid IT infrastructure that supports all the upcoming changes with agility, innovativeness, and security.
To inquire how prepared organizations are for those upcoming requirements arising from Digital 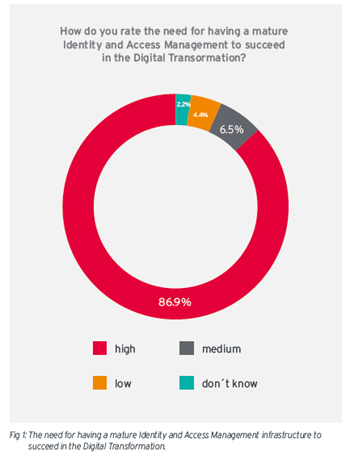 Transformation initiatives such as the need for better managing consumer identities, protecting PII and ensuring that both access to internals and externals to such information is restricted, regardless of whether the information is handled by cloud services or on-premises, KuppingerCole Ltd., an international and independent analyst organization, and CXP Group, an independent European research and advisory firm, conducted a joint survey about the Current State of Identity and Access Management in Organizations on behalf of Beta Systems. The survey has revealed that more than 85 percent of the respondents rated a mature Identity & Access Management (IAM) strategy as highly important for succeeding in the Digital Transformation. It means that a recognition of the need of IAM for business success is not as much of an issue. That being said, the problem is that more than half of the organizations don’t have a mature IAM infrastructure in place, while roundabout two-thirds of the organizations will not have a central management of consumer identities within the next 18– 24 months. Therefore, this article will look at what causes this gap and why it is important for organizations to move forward in their IAM strategies and their deployment.
Transformation initiatives such as the need for better managing consumer identities, protecting PII and ensuring that both access to internals and externals to such information is restricted, regardless of whether the information is handled by cloud services or on-premises, KuppingerCole Ltd., an international and independent analyst organization, and CXP Group, an independent European research and advisory firm, conducted a joint survey about the Current State of Identity and Access Management in Organizations on behalf of Beta Systems. The survey has revealed that more than 85 percent of the respondents rated a mature Identity & Access Management (IAM) strategy as highly important for succeeding in the Digital Transformation. It means that a recognition of the need of IAM for business success is not as much of an issue. That being said, the problem is that more than half of the organizations don’t have a mature IAM infrastructure in place, while roundabout two-thirds of the organizations will not have a central management of consumer identities within the next 18– 24 months. Therefore, this article will look at what causes this gap and why it is important for organizations to move forward in their IAM strategies and their deployment.
What’s IAM?
First things first, let’s look into what identity access management (IAM) is. It is a framework of business policies and technologies for ensuring that the proper people in an enterprise have the appropriate access to technology resources. Therefore, the risk of not having a proper IAM process in place is putting data at risk for being misused, and this situation may result in regulatory non-compliance in the event of an organization being audited.
Identity and access management solutions provide the ability to manage electronic identity for accessing information and resources. In other words, identity management solutions secure content from unauthorized access by injecting authentication layers between the users and the critical apps and data. Protected target resources may include on-premises or SaaS applications and web service APIs across all business scenarios, from business-to-employee (B2E) to B2C. Identity and access management solutions support bring-your-own-device (BYOD), for example, through use social identity integration for purposes of registration, account linking and user authentication. The applications may run on customers' premises or in the cloud.
Lastly, the Identity and access management market is segmented on the basis of the component into password management, audit, authorization, compliance, and governance, single sign-on (SSO), session management, directory services and provisioning. Some of the key players operating in the global Identity and access management market are, Ping Identity, Centrify Corporation, Sailpoint Technologies, Inc., Micro Focus, Hitachi ID Systems, Inc., Okta, Inc., Netiq Corporation, SecureAuth., Microsoft Corporation, Oracle, CA Technologies and IBM Corporation alongside others.
Why Should You Care about IAM?
Taking new regulations such as the upcoming EU GDPR (General Data Protection Regulation) into account, a lack of effective identity and access management poses high risks to compliance.
Increasing usage of bring-your-own-device (BYOD) trends, rising adoption of mobile devices for work, and increasing number of cybercriminals, who get unauthorized access to sites for stealing sensitive data, are some of the factors that drive the identity and access management market. After all, system security and providing secure environment must be one of the top most priorities for the organization. Otherwise, loss of critical information and financial losses may result in very dramatic scenario for any business.
In addition to meeting the requirements of security and regulatory compliance, having a right identity and access management solution also helps organizations with the new business requirements in the Digital Transformation.
Another issue that can be addressed by having a proper identity access management in place is keeping up with employees moving across different roles in an organization. If granted privileges are not revoked as the employee changes her/his duties, all those accesses can accumulate and this situation poses a high risk for so many reasons. First, it makes that person a great target for cyber criminals as her/his excessive privilege represents a great access credential as it is an easy and dirty way to access to broader part of the system simultaneously.
Secondly, it may result in an inside threat as that person may commit data theft. Sometimes, organizations forget about revoking those privileged roles from former employees’ account so much so that a person who is no longer an employee in the organization can still retain those accesses and browse away in the system freely. So onboarding and off-boarding is another main area where IAM technology can support organizations to manage their security risks. Not to encounter with these scenarios, it is critical to have an IAM strategy and a right software deployment.
When you think of all these reasons that prove the relevance of IAM for business success and why organizations should embrace an IAM process, it is hard to understand the factors behind the gap mentioned earlier in this article. However, according to the study conducted by The Insight Partners, low trust factor on cloud services for providing identity assurance is one of the reasons that may slow down the growth of identity and access management solutions among various industry verticals. In conjunction with this concern and the identity and access management market, according to Identity Management Institute, the global cyber security expert shortages of around 1.5 million by 2020 is representing a major risk in this space. To put this into perspective, the institute also notes that more than 200,000 cyber security jobs in the U.S. alone were unfilled in 2015 which was up 74% over the previous five years.
Predictions on IAM
Gartner also published its first-ever Magic Quadrant for Access Management, Worldwide last month. In the report, the Stamford, Conn.-based market research firm predicted that by 2019, more than 80 percent of organizations will use access management software or services, up from 55 percent today.
Gartner created this new report in response to evolving market conditions in the space and explained this: “What was once considered a mature market for web access management that served only web browser clients and web applications using static or semi-static data for access decisions has evolved to one that better supports more diversity in user authentication methods, contextual and adaptive access, mobile computing, internet-connected things and API target systems.”
Additionally, Gartner conducted a survey on IAM program management and technology adoption patterns in September of 2016. Based on that survey data, the research firm found that IDaaS is still the minority delivery model in use today, but the trend is clearly moving toward adoption of IDaaS. IDaaS adoption for new purchases will outpace traditional delivery models by 2021. One of the predictions in the new MQ ties in with this survey data as it elaborates on the growth rate by citing “IDaaS will be the majority access management delivery model for new purchases by 2021, up from less than 20% today.”
Being cited as one of the reasons why organizations should care about IAM, stolen employee passwords is responsible for around 90% of cyber-attacks according to Identity Management Institute, and stolen employee access credentials are predicted to cost businesses about $2 trillion by 2019.
My POV
To thrive in identity and access management system implementation, right off the bat, it is important to see this as a combination of a platform and a strategy, rather than a side project as it is essentially building a solid foundation that organizations will run, the new requirements come with changes in technology and way of doing business. Therefore, choosing the right technology is critical as usual. To make that process less intimidating, organizations can document the primary requirements that the software must address, including emerging technologies that you may consider utilizing in the future. It is also beneficial to audit user activities within the organization as those patterns could portray a bigger picture of the business needs. At that point, it is also valuable to inquire users' needs and concerns regarding the authentication process. After having a better understanding of direct factors, it is also critical to find out how to integrate existing applications into the new platform if needed.

Venus Tamturk
Venus is the Media Reporter for CMS-Connected, with one of her tasks to write thorough articles by creating the most up-to-date and engaging content using B2B digital marketing. She enjoys increasing brand equity and conversion through the strategic use of social media channels and integrated media marketing plans.